Is it time to De-Throne the Password?

Wishing all a very Happy new Year !!!
Looking back into 2015, we have had a year with one of the highest number of password breaches in the decade so much so that not even password managers were spared...
I am not worried.. My passwords are very complex..
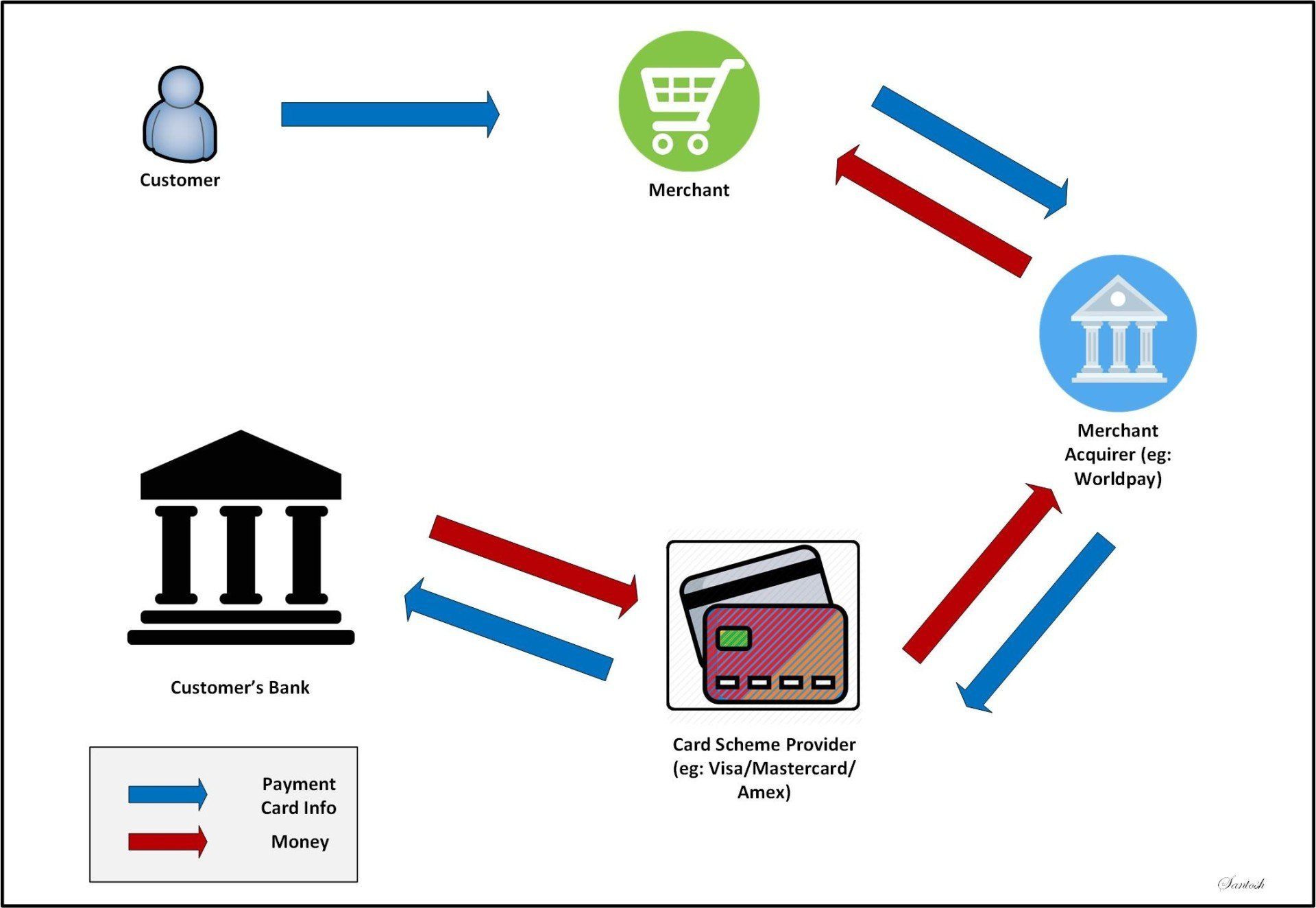
Much has been talked around the wider security circle on the importance of having strong & complex passwords. A good authentication system should allow access to protected resource to those who are authorised while keeping those who are not authorised away. Both these aspect are equally important. If implementing an authentication system that allowed an unauthorised person to access protected resource is a failure, it is equally a failure if the very same system puts off genuine users by virtue of having highly complicated and restrictive authentication requirements.There needs to be a perfect balance between security and usability.
Password based authentication is the most used since it also is the easiest to implement. For most part of the last decade, the security fraternity has been emphasising users to use complex passwords that are hard to guess. Add to the fact that on an average we use well over 20 passwords. With a convoluted passwords comes the issue of users forgetting these passwords, re-using it across many systems and in some cases writing it down on sticky notes (physical or virtual). They are very hard to type in on mobile devices (particularly if you have a complex one).
Talking about password re-use, there is growing number of enterprise users who re-use passwords between their personal identities (like Facebook, LinkedIn or even a not-so-secure website that gave them a free usb stick for registering at a trade show) and corporate identities leave alone it being complex enough or not. If any of these websites are compromised, with a bit of social re-engineering, the user's corporate access could also be compromised.
What was appropriate as a excellent way to authenticate users a decade ago may not be safe enough in the current climate. Hackers empowered with computers with extremely high processing power working in tandem on P2P systems make even a complex password to be cracked in a jiffy with a fairly high success rate. Passwords have an inherent risk that they can be compromised by Phishing, Key-logger or Malware. All these make password one of the weakest forms of authentication scoring low on security as well as usability.
How about if i use something along with the passwords to make it safer?
From the discussions above,we could understand that relying on password as the sole means to protect access to resources is not secure enough in today's climate. While not having to use password as a factor at all would be the perfect situation, a good place to start would be to use the security provided by passwords further enhanced by adding additional layers of authentication factors. This will involve the user to provide two or more factors of authentication which would be a combination of:
- something the user know (Password, Pin etc.),
- something the user has (Smartcard, KeyFob, Soft-Token, YubiKey, X.509 certificate etc.) and/or
- something the user is (Fingerprint, Iris recognition, Voice pattern etc.).
This stronger authentication is known as Multi-factor Authentication. The general guidelines is to have a mixture of the factors belonging to different types i.e Password + Keyfob.
The purpose of authentication is to arrive with a level of assurance that the person authenticating is who he claims to be. Making use of multi-factor can increase the score of how assured you are about the person authenticating. That said, each type of authentication factor can provide a different level of assurance. For example, proving using " What you have
" is usually more assuring than proving using " What you know
" and similarly, " What you are
" provides a higher level of assurance than the other factors.
This can lead us to an interesting use of multi-factor where a particular authentication factor could be utilised based on a risk-based approach. So, if a HR executive is accessing the corporate HR application from within the corporate network, he might need to provide only his password to authenticate, but if he is accessing the same application from a coffee shop down the road, the risk profile is higher, hence he might be expected to provide a OTP from the keyfob or a Soft-Token and if he is changing any personnel records while being logged- in outside the corporate network, he may need to provide additional
authentication factors like Fingerprint as the risk profile has increased further. This is known as " Step-Up
" Authentication.
The issue of users forgetting password due to having to remember many passwords is addressed to a great extent by using password managers. Enterprises address this using Single-SignOn (SSO) solutions. But this does not address the weakness of password as something that can compromised by Phishing, Malware or the fact that with cracking of passwords is made easier in the current climate of co-ordinated attempts using P2P etc.
Sounds great..but can't we do anything about the password element in the above?
Yes.There are solutions emerging in this space.. In my next post i will be covering around how we could move towards eliminating the need for using password...
#KillPasswords